I am posting this as this image was in my desktop for years. I want to delete it, so thought of adding it to blog.
In 2006, one of my linux server got hacked. Most will tell you need OS restore when you got hacked. I do not want to restore the OS as its lot of work. So i started with firewall. Blocked all ports other than that of needed services like apache, mail, control panel, etc.. Disabled access to SSH port and allowed only my IP connected to SSH.
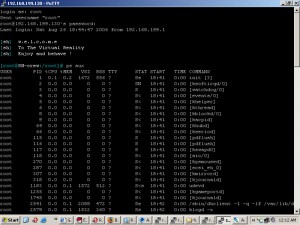
Then check the server with rkhunter and chkrootkit and found SHV5 rootkit was installed on the server. So i have installed SHV5 rootkit on my local PC ans study it. Here is a screen shot of my local SHV5 rootkit installation. Then i try uninstall the rootkit on my local pc and verified it really un installed. Then i done the same thing on the server and i monitor it for next few days. Nothing happened, server worked fine for long time. This was caused by an older kernel on the server + some insecure scripts used by the clients.


2 Responses to SHV5 rootkit