Author Archives: Annie
About Annie
I've been working in Technical Section for over 10 years in a wide range of tech jobs from Tech Support to Software Testing. I started writing blog for my future reference and useful for all.Check Linux Memory Usage Using “Free” Command
Free command displays information about the physical (RAM) and swap memory of your system. In the example below, the total physical memory displayed below are in KB. The following example will display the total memory on your system including RAM
How to upgrade Clientexec
Here is the step by step instruction for upgrading client exec to the latest version. 1. Download the latest version of Client Exec from their site. (https://www.clientexec.com/download.php) 2. Login to the web hosting control panel and download the MySQL backup
How to check inode usage on linux system
You can Check the inode usage on server using the below command and see how many used inodes there are. # df -i The flag -i is used for displaying Inode information. Sample Output :-
How to Show hidden files in Windows 8
By default hidden files and folders are not visible and this is a preferred way for most users. But you can easily show hidden files and folders. * From the Windows 8 Start Screen, click on the Control Panel icon.
Find Files Using Name in Current Directory
Find Files Using Name in Current Directory Find all the files whose name is “wp-config.php” in a current working directory. This command result all wordpress sites hosted in server. Find all the files whose name is del.php and contains both
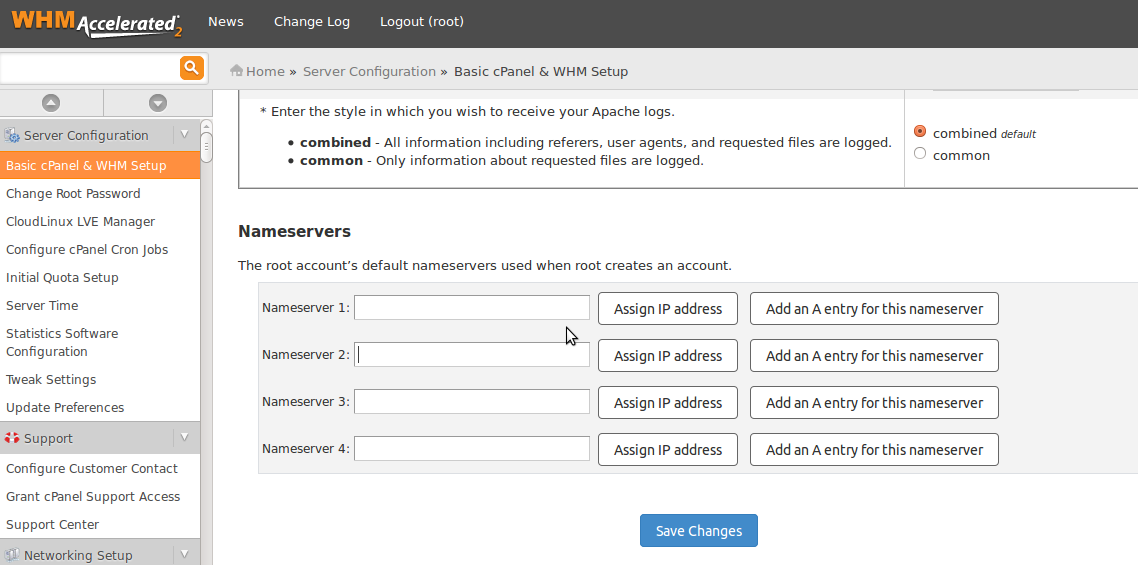
Setting Up Private Nameservers in WHM/cPanel
1. Log in to your server’s WHM interface and find the navigation section on the left called Basic cPanel & WHM Setup, under Server Configuration. 2. When you load this screen for the first time you may see that two
Best Free Business Apps for the iPhone
Timesheeter One of my favorite apps, Timesheeter tracks your time and projects. View daily, weekly, monthly and overall statistics in pie charts, track your expenses, log time with time clock, export your data as Excel (CSV), TXT or PDF to
How to check cPanel/WHM version via SSH
To check cPanel/WHM version via SSH, you need to run following command. cat /usr/local/cpanel/version or /usr/local/cpanel/cpanel -V
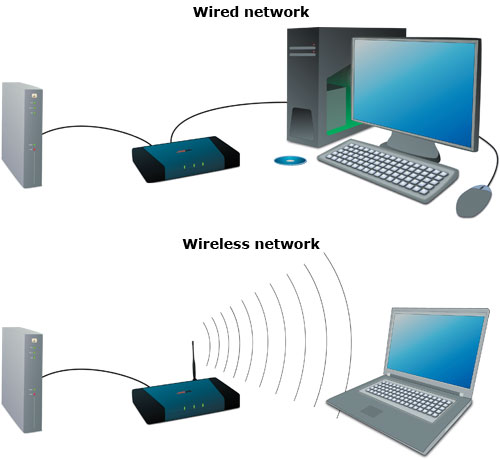
Types of Networks in Computer System
A network is basically all of the components (hardware and software) involved in connecting computers across small and large distances. Networks are used to provide easy access to information, thus increasing productivity for users. eg. File Sharing , Resource Sharing
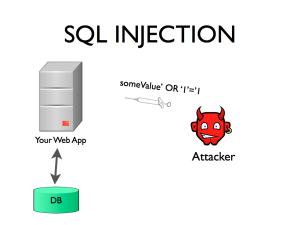
What is SQL Injection
SQL Injection is a type of web application security vulnerability in which an attacker is able to submit a database SQL command which is executed by a web application, exposing the back-end database. A SQL Injection attack can occur when