Category Archives: Cpanel Server
What is CloudLinux?
CloudLinux is a linux based operating system that creates a stable hosting environment for all of our web and reseller hosting customers. It is able to keep a single account from overwhelming a server and causing slow performance or downtime.
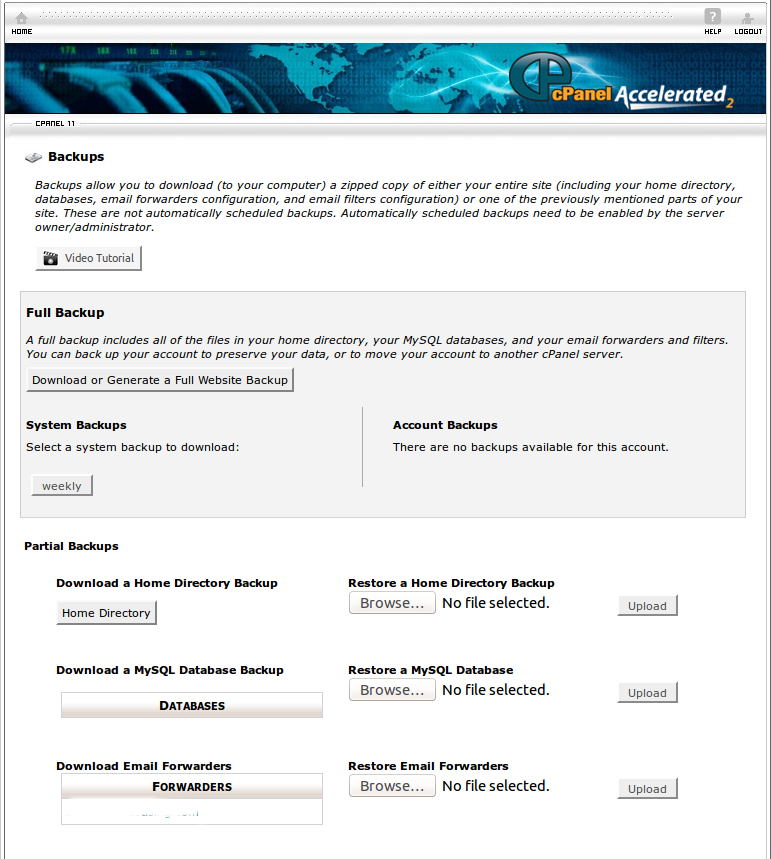
How to use cPanel Backup/Restore option
Login to cPanel and navigate to Backup button under ‘Files’ Menu (Home > Files > Backup) It will show you the below page: The Backup Wizard is very user-friendly interface for creating a backup of the entire site, a partial
Fixing Cpanel WHM expired SSL certificate
A customer had SSL certificate installed on his servers hostname for WHM and Cpanel. Recently SSH got expired. So he can’t access WHM. Got this fixed by
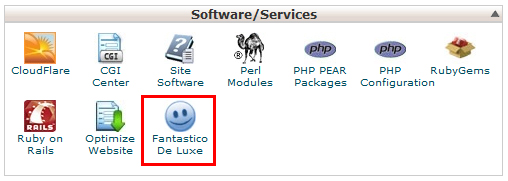
How to Uninstall Fantastico from WHM / cPanel Server
How to Uninstall Fantastico from WHM / cPanel Server Log into your server via SSH as root and execute the following: The first line, /var/netenberg/ should be replaced with whatever directory you installed the Fantastico master files ( /home/netenberg/ )
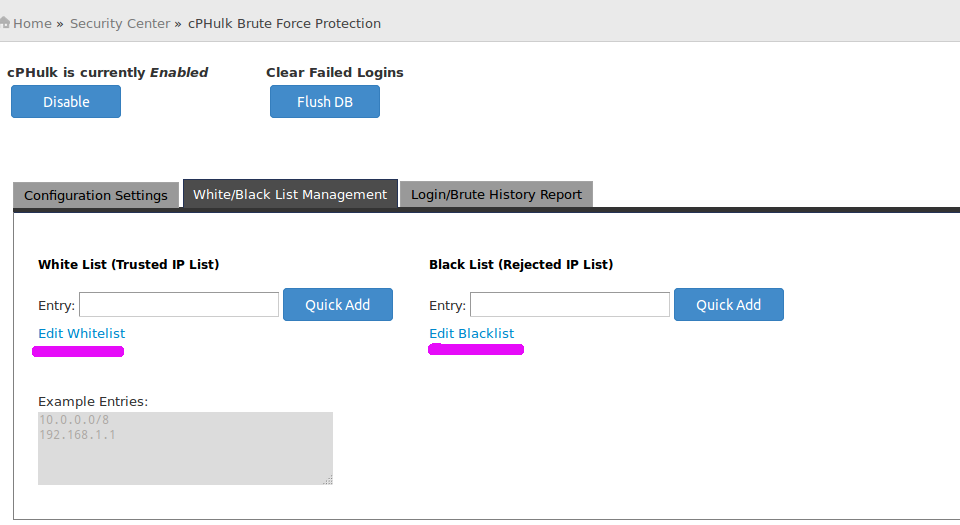
cPHulk Brute Force Protection
Brute force is an hacking method that involves using an automated system to guess the password to your web server or services. cPHulk provides a security protection against Brute Force attacks for FTP, cPanel/WHM and SSH. How to enable cPHulk
Install WordPress in less than Five Minutes through cPanel
WordPress is web software you can use to create a beautiful website or blog. We like to say that WordPress is both free and priceless at the same time. Fantastico-De-Luxe is one-click script install software available in cPanel, through you
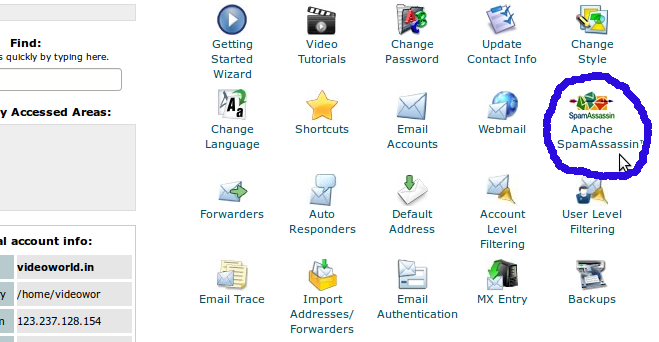
How to enable SpamAssassin in cPanel/WHM
How to enable SpamAssassin in cPanel/WHM Spam filters are a very important part of any mail server. To configure SpamAssassin, please follow the steps below: Click on the SpamAssassin icon on the main screen of your cPanel interface. To enable
Cpanel: An error occurred while processing this directive
I got the following error message on top of the package creation box in WHM. (WHM > Add packages) [an error occurred while processing this directive] Error log (tail /usr/local/cpanel/logs/error_log) shows I had rebooted the server and also run fixquotas
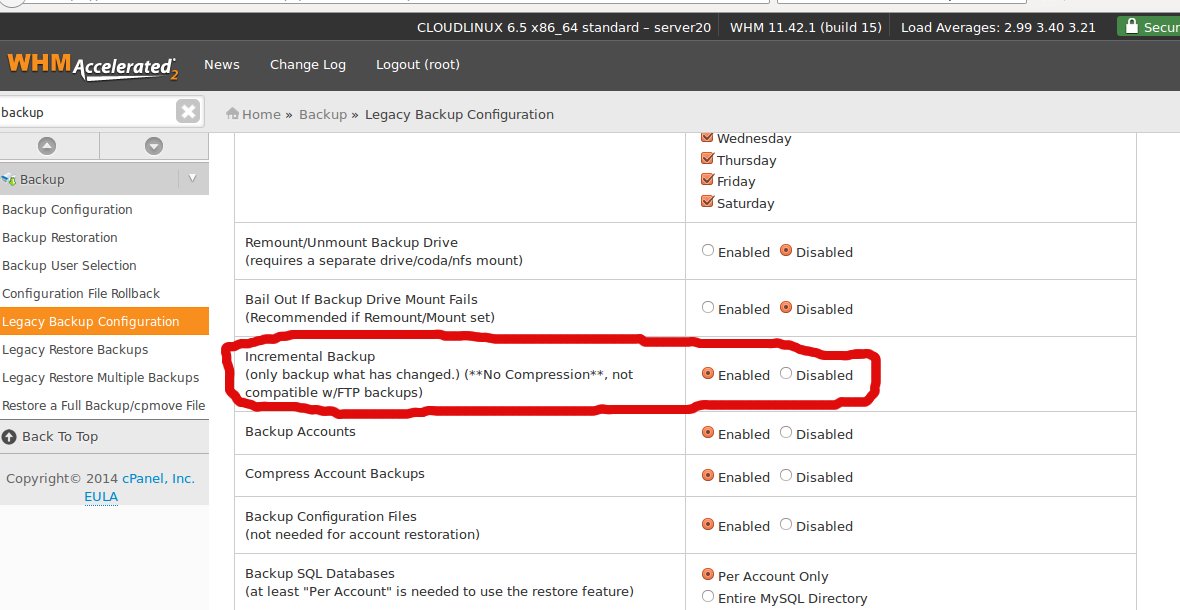
Enable Incremental Backup in WHM
You can use the Legacy Backup Configuration feature in WHM Home >> Backup >> Legacy Backup Configuration Enable Incremental Backup option and click on Save button.
How to keep Hackers Away
1. Do not disable safe_mode under php.ini. If customer requested t disable it, turn it off on his account only. As most of the time attack is done using c99 php shell scripts. This c99 shell allows an attacker to